Everything About ETTVI’s Online Md5 Generator
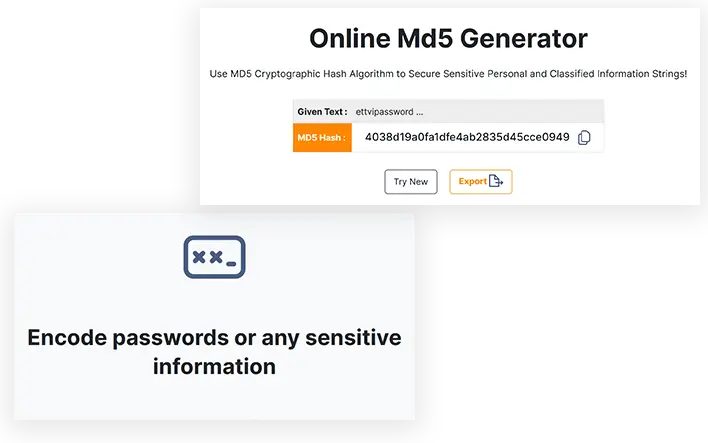
ETTVI's Md5 Generator Tool provides an easy method for converting your character string into a MD5 hash and validating it using MD5 or the Message-Digest Algorithm 5. Using ETTVI's Online Md5 generator, passwords can be encrypted with the help of strong encryption. This is done as a security measure because it enables one to ensure that files downloaded from websites have not been altered in any way.
It comes with various features to provide a seamless user experience.
Generate upto 40 Md5 code at a timeGenerate 40 Md5 code at a time with ETTVI’s Online Md5 generator. Enter 40 characters in separate lines on the search bar of the tool and hit the “Export” button. You will get 40 Md5 string 32 characters in hexadecimal format.
Free to use toolETTVI’s Online Md5 generator is a free to use tool. You don't have to spend a single penny to get all its features and results. Use it anywhere, any time and anyplace you want.
24/7 customer support
ETTVI’s Online Md5 generator provides 24/7 customer service for its users. In case the tool has stopped working or shows incomplete results contact ETTVI customer support and we will try to resolve the issue within 24 hrs.
What exactly is Md5 string, and why do people need it?
Why is Md5 getting so much attention?
An MD5 algorithm is a cryptographic hashing algorithm, or "message digest", that has been used since 1993. It will be possible to generate a hash from digits by applying a one-way algorithm and then selecting those digits. When information or media must be safeguarded, message digests (Md5) are the most common method to accomplish that task. A message can be inspected with this feature to determine if any of the key parts of the message have been changed or updated.
The message digest (Md5) is a one-way hash function used to create a fixed length hash value from a random array of data.
What is the purpose of Md5?
During cryptography, MD5 serves principally as a hashing algorithm. Contrary to a hash function, which consists of forming a fixed-size bit string from a series of data blocks and turning them into a hash value. Message direct (Md5) functions compute hash values for data sets by comparing them with a hash function. Together with other hash functions, Md5 is often used for digital signatures and message verification codes. Further, it's used to check for data corruption, detect duplicate data, and identify files.
Despite being able to produce the same result again and again for a given dataset, Md5 hashes are used to verify data integrity. A MD5 user can compare the hash of the data source with a hash created on the same destination of the file with which they will compare the hash. In this way, the hash can be verified to ensure that it was not altered or tampered with.
By creating a Md5 hash, you are NOT encrypting the data, but creating a fingerprint of the data. If the generated MD5 hash is reversible, the user cannot recover the original string. This implies that the generated MD5 hash cannot be reversed.
Is it possible to decrypt Md5?
Because MD5 is not an encryption algorithm, you are unable to decrypt it. It is widely believed that MD5 is capable of encrypting data, but this is not true. In actuality, MD5 does not provide data encryption. The tool is only capable of calculating a hash value for a specific set of data.
Is Md5 a truly secure function?
It's true that MD5 has traditionally been viewed as a crash-prone algorithm. In reality, using Md5 depends greatly on how and where this algorithm is utilized. In order to generate an Md5 hash, a string may be arbitrary and encoded into a 128-bit fingerprint. In case that you are writing the same strings using the Md5 hash generator, you will always end up with the same 128-bit result.
For creating and storing passwords, MasterCard numbers, and other kinds of sensitive information, MD5 hashes are usually used with little strings like passwords or strings of characters.
In other words, it has proved effective for use as a way to check the integrity of a database table when MD5 is being applied only as a basic checksum algorithm. If Md5 contained only 32 digits, it would be an extremely compact algorithm. Therefore, the hash can be calculated immediately without requiring a lot of memory or storage space to calculate. Unless carefully supervised, do not use MD5 for password summarization or any other security systems that are very important. You can find a great deal of information on the Internet regarding Md5 guidelines to secure your data. Hopefully you will be able to use Md5 correctly after reading these guidelines.